Cloud Services Infrastructure
Compliance Programme
Experian have implemented a comprehensive set of Global Information Security policies which are based on ISO 27001 and covers key topics such as: Access Control, Asset Classification, Systems Development, Cloud and Third Party.
Experian leverages the three lines of defence risk management methodology to maintain the appropriate security controls. This is built up of:
- the first line of defence which is responsible for the day-to-day operations
- the second line which provide oversight, guidance and internal assurance
- and final the third line of defence which is our independent internal audit
Experian has achieved and subsequently retained certification to ISO/IEC 27001, having successfully made the transition from BS 7799.
Service Continuity
The Experian One Platform is intended as a real-time 24x7 global service. To support operations, Experian has a Business Continuity framework that is structured around the international standard framework for Business Continuity Management (BCM) and ISO22301, ensuring we meet the high standards necessary to continue operations regardless of the operating location. All plans are based on methodical analysis to ensure the ongoing delivery of critical processes and services.
Outputs from analysis are used to develop and document detailed plans and associated procedures for service recovery and ongoing delivery to acceptable service levels in the event of a major incident. As part of the annual maintenance programme Business Continuity plans are reviewed on an annual basis (as a minimum) with continuity exercises used to validate them.
The Crisis Management Team are on 24-hour call-out, and availability is collated and distributed on a weekly basis to ensure that the operational effectiveness of the group is not compromised.
Physical Locations
The Experian One Platform is part of the Experian API product set, providing decision processing from 7 locations. Each is an independent system with local processing capability co-located with data storage.
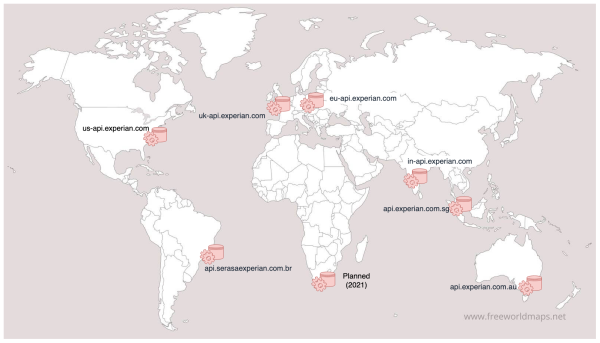
Physical data centres hosting components of the platform are either run by Experian or Amazon Web Services. All locations have ISO 27001 certification for data centre operations and are suitable to be part of a Payment Card Industry (PCI) cardholder data environment.
Network Security
The Experian API products are internet services accessed over https (TLS v1.2+). Web Application Firewall and Denial of Service protection is at the network perimeter, with mutually authenticated connections reaching into the Kubernetes cluster. Behind the perimeter security defences there are network security controls, plus an API Gateway that works in concert with Kubernetes networking to forward requests to the appropriate service instances running within the access-controlled compartments.
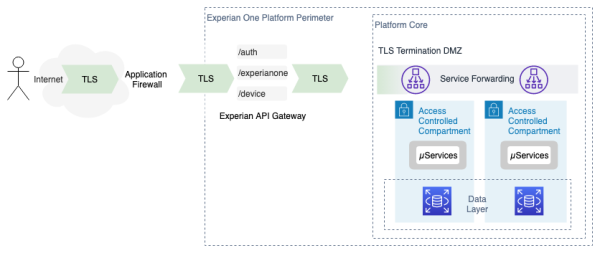
Access rights are validated at multiple stages from the perimeter through to the individual service instance to maintain the integrity of the execution compartment. Security controls are designed to be redundant where failure of controls at any single layer does not expose the platform or data.
Platform Architecture
The Experian One Platform is composed of microservices running on a distributed Kubernetes container platform deployed across multiple data centres for availability, auto scaling & geo redundancy. Every service, no matter how small, is maintained with a minimum of two executables on different compute nodes in different physical data centres. We lean on large scale cloud infrastructure providers to achieve our service availability targets.
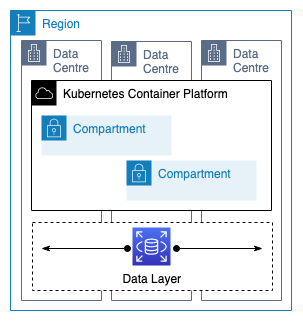
As far as possible the locations are identical with some differences in local networking and processing topology. In North America and the UK regions, the processing cluster is split between the local Experian data centres and the local Amazon Web Services (AWS) Region. In other regions the cluster is run exclusively in AWS across multiple availability zones, benefiting from the availability and uptime performance of those services. The data layer is provided by AWS with multi-AZ clusters and data redundantly stored across all of the regional location. It is only accessible from the container cluster and a dedicated support infrastructure protected by privileged access control systems.
Support access
The Experian One Platform support organisation is responsible for monitoring the health of services and managing continuous upgrades. The security of the system is monitored from the Experian Security Operations Centre (SOC). Alongside continuous monitoring of activity from across the network, the SOC provides Incident Response and Threat Intelligence. There is no access to the running operating system and support engineers do not hold the ability to modify running services, but can obtain access to the data layer for support purposes if an incident requires it.
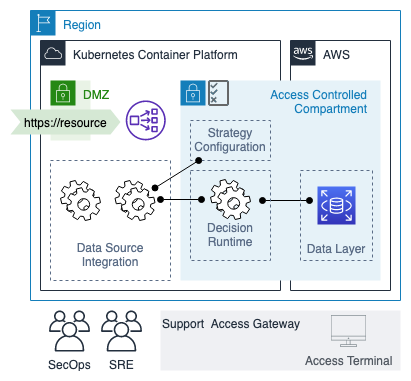
Machine-generated data layer credentials are stored in a secure password vault and loaded into process memory at runtime. Accessing the data storage as part of an escalation process requires the support engineer to connect to a privileged access management system using multi-factor authentication before accessing the database itself. Neither password vault nor database are accessible without temporary access being granted. Requesting and using access is recorded.
Software Development Lifecycle
Security issues in software can be discovered at any time, and the design principle of Experian One is to enable rapid and consistent deployment of updates. Standardising the assembly of services into immutable container images as part of larger deployable components supports this principle. All development is subject to Code Quality and Static Application Security Testing which enforces rules based on common coding best practices derived from OWASP Top 10, SANS 25 and PCI-DSS. All developers work in teams to carry out peer code review, and the automated static analysis is carried out on a continuous basis. The process includes cross-referencing 3rd party components to known vulnerabilities so that they can be remediated as they are announced. Dynamic analysis of every microservice is carried out as part of each update and there is regular manual testing of the end-to-end system.
| Assessment | Frequency |
|---|---|
| Peer Review | Continuous. |
| Static Code Scan | Continuous per microservice release. |
| Dynamic Scan | Continuous per component release. |
| Manual Test | Ongoing against platform with independent testing scheduled annually. |
Using Common Vulnerability Scoring System (CVSS) scoring, issues graded Medium and above discovered during development are resolved before release while issues discovered in release versions are resolved according to the timeline below.
| Issue Severity | Time to Fix |
|---|---|
| Critical | 30 days |
| High | 60 days |
| Medium | 90 days |
| Low | 90 days |