Identity and Access Management
Identity Architecture
There are two mechanisms to interact with the Experian One Platform API; Bearer tokens and Hash-based Message Authentication Code (HMAC) signed requests.
Bearer tokens
Access to the Experian One Platform services requires a Bearer token to be included in the request, and a valid identity is required to obtain this token. The Experian One Platform leans on the Experian B2B identity provider, with user management (a management activity through a custom interface Experian Web Access Control System). Federation of user authentication via Security Assertion Markup Language (SAML) 2.0 for local evaluation of user authentication is supported.
Each Region has an assigned Identity Provider (IdP) and a single Authority trusted by all microservices. This generates and signs access tokens that are valid for a fixed duration.
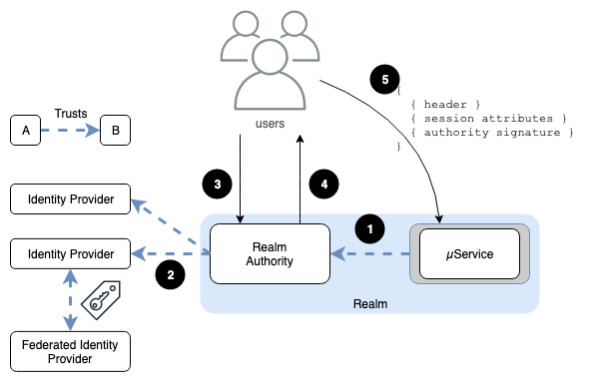
- Each microservice holds the keys necessary to validate the signatures of tokens issued by the Realm Authority.
- The Realm Authority trusts at least one Identity Provider (IdP) which can in turn be federated with other IdP.
- Requests for Access Tokens require credentials that are managed by one of the trusted IdP.
- The Authority generates a Bearer token (signed JSON Web Token) that encapsulates the capabilities of the session.
- A valid Bearer token must be supplied in the Authorization header of every API call. Each microservice will validate the token signature and then decide whether or not to execute the request.
Signed requests
A second pattern of authentication is used in machine-centric products, where HMAC keys are distributed and used to sign the request payload. This provides identifying information as well as validating the integrity of the request.
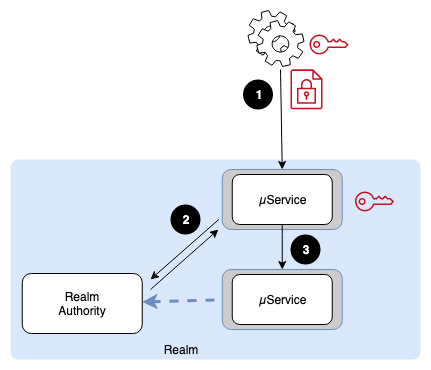
- Each client service is provided with an HMAC key that it uses to sign the request payload.
- The receiving microservice has access to the same key and can use it to identify the calling service. With this information, it can request a JWT that allows the request to be processed.
- The request is passed to the execution context.
Identity Management
The Experian One Platform is designed to support different identity management delegation approaches, from Experian-managed to Federated.
Manually provisioned and managed.
There is a formal user registration and deregistration procedure in place managed by the Global Security Administration function which is certified to ISO 27001:2013. Each process involves gaining sign off from the person responsible for the system then actioning the request in a manner that is fully auditable. Regular reviews of user access rights are performed to identify and remove any invalid or inactive accounts.
User identities require a valid email account that is used during the setup and password recovery. User credentials follow common enterprise rules for password quality and age. Multi-factor authentication using Security Questions, or a one-time password (OTP) device is supported. Experian have information stewards who perform regular reviews of user access rights for their respective systems to identify and remove invalid or inactive users and accounts. These reviews are carried out yearly as a minimum for normal users and quarterly for internal support users.
| Location of identity | Experian Identity Provider |
| Location of credentials | Experian Identity Provider |
| Provisioned by | Experian Global Security Administration |
| Access Profile | Managed by Experian, supported by designated Client Administrator |
Federated authentication with manual provisioning
Federation of user authentication via SAML is supported. Experian is responsible for management of ad-hoc changes requested by the client. Annual review are supported by a designated Client Administrator.
| Location of identity | Experian Identity Provider |
| Location of credentials | Client Identity Provider, using federated browser access |
| Provisioned by | Experian Global Security Administration |
| Access Profile | Managed by Experian, supported by designated Client Administrator |
Service Credentials
Non-interactive service identities may have non-expiring passwords but additional IP access controls are recommended in this case.
Access Management
Access to different Experian One Platform services is managed by assigning roles to the identity. Most roles are product-specific, with a small number of standard roles within the Platform.
| Platform Roles | |
|---|---|
| Administrator | Administrative role that includes all administrative functionality covering the management and configuration of the subscribed products. |
| BI Manager | Access to view and configure reports. |
| BI Analyst / BI Viewer | Access to view reports. |
| Auditor | Read only access to configuration and reports. |
| Customer Acquisitions Roles | |
|---|---|
| Risk Manager | Manage tactical and dynamic parameters. View user decisioning reports. Deployment of tactical parameters into production and management of dynamic parameters. |
| Risk Analyst | Manage tactical parameters and decisioning strategy. View non-specific decisioning reports. |
| Fraud Manager | Access to operational reports, data viewer, and application notes and attachments. Able to delete attachments. |
| Fraud Analyst | Access to operational reports, data viewer, and application notes and attachments. |
| Underwriter | Multiple underwriter levels typically exist within the strategy workflow. An Underwriter can typically view applications, attachments and reports. |
| Operations Analyst | View operational reports. Create, read, and update attachments. |
| Operations Manager | Create, read, update and delete exports and attachments. Manage batch jobs. |
| Collections Essentials Roles | |
|---|---|
| Collections Manager |
System and process expert. Fixing system issues and providing workarounds to ensure Collections agents can focus on the task of collections with customers. Training and user system knowledge. May be required to perform within a Collections agent capacity. |
| Collections Supervisor | Implements successful collection strategies for dealing with collections customers. Meets performance targets (collection KPIs) and provides efficiency and quality while developing and maintaining high levels of customer satisfaction. |
| Back Office Collections Agent |
Responsible for correspondence and escalated cases from Collections agents. Often required to ‘own’ cases and be the point of contact for the customer until there is a resolution. Works the queue of identified special cases. Provides a high level of customer service through efficient collection initiatives and the appropriate treatment of customers, ensuring high levels of restored debt. |
| Collections Agent |
Responsible for correspondence and calls from and to customers who are either due or over the limit on their accounts, agree payments and arrange repayment plans, if necessary. Provides a high level of customer service through efficient collection initiatives and the appropriate treatment of customers, ensuring high levels of restored debt. |
| CrossCore Roles | |
|---|---|
| Case Manager | Search and view case results, case details and queues. Update fraud status of cases. |
| Event Viewer | Search and view case results and case details. |
| Queue Manager | Create, update and delete queues. Manage queue assignments for investigation. |
| Reporting Viewer | View case dashboard and operational reports. |
| Workflow Manager | Create, update and delete workflows. |
| Workflow Viewer | View workflows. |